
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to Website Planet about a non-password-protected database that contained over 86,000 records belonging to ESHYFT — a New-Jersey-based HealthTech company that operates in 29 states. It offers a mobile app platform that connects healthcare facilities with healthcare workers, including Certified Nursing Assistants (CNAs), Licensed Practical Nurses (LPNs), and Registered Nurses (RNs).
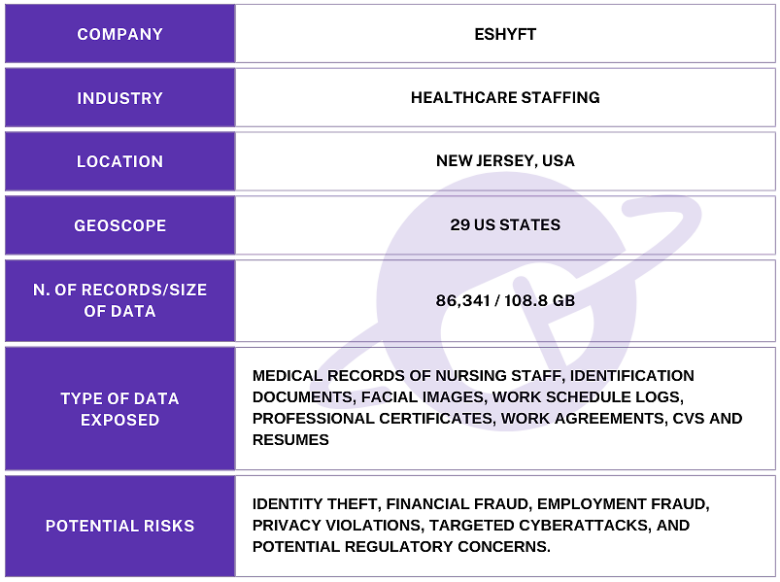
The publicly exposed database was not password-protected or encrypted. It contained 86,341 records totaling 108.8 GB in size. The majority of the documents were contained inside of a folder labeled “App”. In a limited sampling of the exposed documents, I saw records that included profile or facial images of users, .csv files with monthly work schedule logs, professional certificates, work assignment agreements, CVs and resumes that contained additional PII. One single spreadsheet document contained 800,000+ entries that detailed the nurse’s internal IDs, facility name, time and date of shifts, hours worked, and more.
I also saw what appeared to be medical documents uploaded to the app. These files were potentially uploaded as proof for why individual nurses missed shifts or took sick leave. These medical documents included medical reports containing information of diagnosis, prescriptions, or treatments that could potentially fall under the ambit of HIPAA regulations.
The name of the database as well as the documents inside it indicated that the records belonged to ESHYFT. I immediately sent a responsible disclosure notice to the company, and the database was restricted from public access over a month later. I received a response thanking me for the notification stating: “Thank you! we’re actively looking into this and working on a solution”. It is not known if the database was owned and managed by ESHYFT directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
ESHYFT provides a mobile platform that connects healthcare facilities with qualified nursing professionals. It is available on both Apple’s App Store and the Google Play Store. Apple no longer provides user statistics, but the ESHYFT app has been downloaded more than 50,000 times from the Google Play Store.
The application claims to offer nurses the flexibility to select shifts that fit their schedules while providing healthcare facilities with access to vetted W-2 nursing staff to meet their needs. The platform is available in following U.S. states: AL, AZ, AR, CA, CT, DE, FL, GA, IL, IN, IA, KS, KY, MD, MI, MN, MO, NE, NJ, OH, PA, RI, SC, TN, VT, VA, WA, WI, and WV.






24 Comments
gnabgib
Title: Thousands of Records, Including PII, Exposed Online in Healthcare Marketplace Connecting Facilities and Nurses Data Leak
(vs current: "'Uber for nurses' exposes 86K+ medical records, PII via open S3 bucket")
booi
Uber for ___ has lost all meaning
dartos
Well there be any consequences for the company?
ethagnawl
I'll need to dig up a source but I recently heard about this company and, apparently, before offering gigs they do a credit report to determine how much debt the person is carrying (i.e. how desperate they are) and they use that information to _round down_ the hourly rate they offer them.
In the unlikely event that there are any negative consequences for this breach, they deserve every bit of them and more.
marcus0x62
Move fast and violate HIPAA.
jppope
Worth mentioning, because the authority level of medical practitioners throws people off. Don't ever give a doctor or practice your Social Security Number. They don't need it. Similarly if they want to check an ID that doesn't mean scan or photograph. Doctors, practices, etc are the worst at infosec. They have no training, basically no penalties if they do something wrong and all of that info is only to follow up in case you don't pay your bill.
gtirloni
Why "Uber for nurses" and not the actual company name in the title?
mhitza
I wonder how old the S3 bucket was, because at some point AWS made new S3 buckets private by default.
Which means it's either old, or they recklessly opened it up because they couldn't get files uploaded/downloaded to the bucket from their mobile app/services.
CaffeineLD50
Yeah I remember when Amazons AWS was new and people said "hey its cool but not secure." Then AWS added all these security features but added a caveat: BTW security is your responsibility
Here we are. I guess we can blame the users and not any shitty security architecture slapped on AWS.
Clearly what matters most is that legal culpability be avoided, not that users will be secure. The former is 'shite security' while the latter is good security
jihadjihad
In the section of their Privacy Policy titled Data Security [0]:
> We use certain physical, managerial, and technical safeguards that are designed to improve the integrity and security of information that we collect and maintain. Please be aware that no security measures are perfect or impenetrable. We cannot and do not guarantee that information about you will not be accessed, viewed, disclosed, altered, or destroyed by breach of any of our physical, technical, or
managerial safeguards. In particular, the Service is NOT designed to store or secure information that could be deemed to be Protected Health Information as defined by the Health Insurance Portability and Accountability Act of 1996 (“HIPAA”).
IANAL and all that, but I’m not sure you can use the excuse “We didn’t design our system to be HIPAA compliant, sorry,” and hope your liability disappears. Does anyone know?
0: https://eshyft.com/wp-content/uploads/2019/06/ESHYFT-Privacy…
ripped_britches
What makes this uber for nurses?
dikaio
Would be surprised if this company makes it out of this. Medical records…. Yikes
SamuelAdams
I am confused, the article seems to be short on details. Was the attack an open S3 bucket? The company in question seems to be hiring for GCP, so I imagine they don’t use S3 at all.
Did the submitter intentionally change the post title to get more clicks?
https://eshyft.com/careers/gcp-devops-engineer/
whatever1
I thought the cloud was safe, that is why you pay premium.
markus_zhang
What a surprise. How do we, the common people dealing with corporations and governments leaking out information left and right? Even password storage services are not really safe AFAIK.
999900000999
Are y'all gonna blame AWS like you blamed Firebase last week ?
The security procedures I take while hacking out something for my friends at 3am should not extend to products hosting PII. It's up to YOU to implement basic data security.
bigfatfrock
Sorry for the dude that built their infra and was really tired and then woke up to this, what a bummer.
elevatedastalt
Annual reminder that the P in HIPAA stands for Portability, not Privacy.
RobotToaster
Why does this keep happening? It seems like every month there's a new leak from an open S3 bucket?
j45
I wish private data was more independently audited.
hrhbbvjhcxb
[dead]
albert_e
The linked article does not mention Amazon S3 or AWS
Is there a different source for the "open S3 bucket" in HN title?
bn-l
Always. Always the open bucket.
tmpz22
Are we pretending that there are still functional regulatory agencies that are able to take action over this?