Hacking. Disinformation. Surveillance. CYBER is Motherboard’s podcast and reporting on the dark underbelly of the internet.
“Activation Lock,” a message displayed across the iPhone’s screen read. “This iPhone is linked to an Apple ID. Enter the Apple ID and password that were used to set up this iPhone.”
This lock essentially turns iPhones into very expensive paperweights until the owner enters the requested credentials. The feature is designed to stop anyone else from using the phone if it’s lost, or thieves from making money by reselling a stolen device. In part, Activation Lock is intended to make iPhones less attractive to thieves because stolen devices can’t be used.
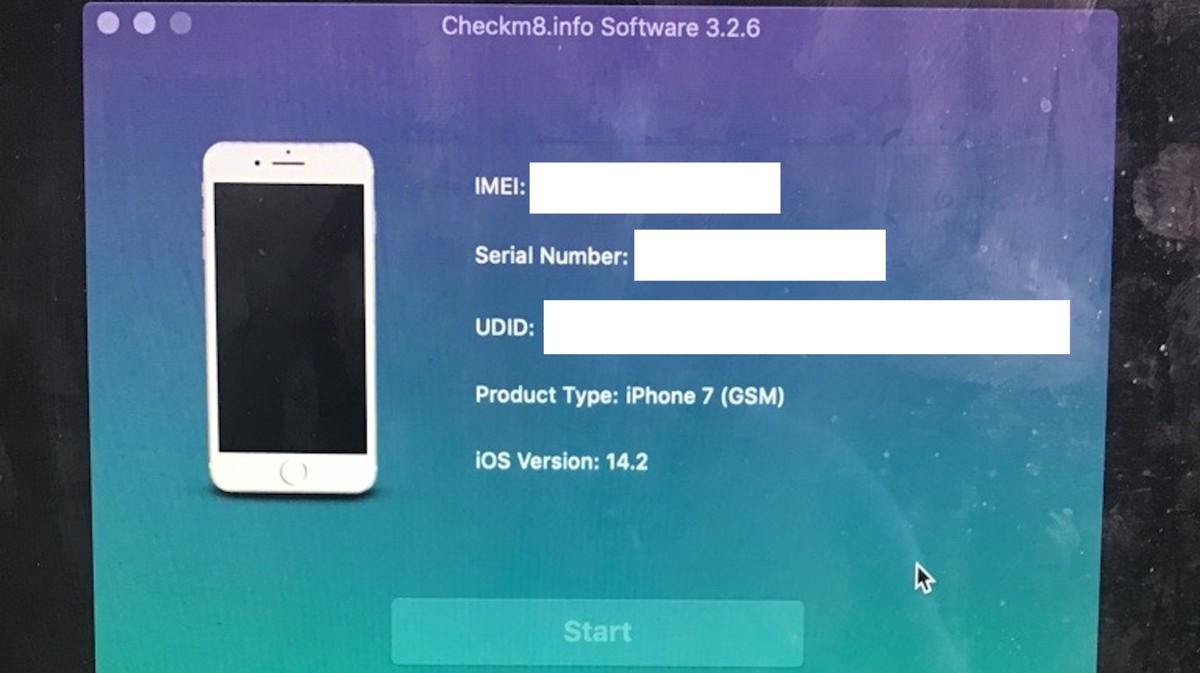
Now, an underground group is offering people a way to strip that lock from certain iPhones with its pay-for-hacking service. iOS security experts suspect it is being used to remove protections from stolen iPhones. The hacking group called Checkm8.info offering the service, which lifts its name from a popular free-to-use jailbreak, insists its tool cannot be used by thieves.
“Our goal is the ability to repair electronics as it’s the key to saving resources, tackling e-waste and environmental damage,” the administrator of Checkm8.info told Motherboard in an email. Motherboard has previously written about how criminals have used phishing emails to grab necessary login credentials to remove the Activation Lock. Checkm8.info provides a much easier method, and appears to streamline what is ordinarily a complicated process into one that non-technical users can follow. Checkm8.info is correct in that Activation Lock can be frustrating to iPhone repair professionals, electronic waste facilities, and refurbishers, and has caused many perfectly good phones obtained through legal means to be shredded or destroyed. A user of the Checkm8.info site told Motherboard they used the service as part of their legal phone reselling business.
Do you have more information on criminals using Activation Lock bypass tools? We’d love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
Under the hood, Checkm8.info is using checkra1n, an open source jailbreaking tool released in 2019. Checkra1n uses an exploit called checkm8 written by the developer known as Axi0mX.
“I don’t like it, but I don’t know what I can do about it,” Axi0mX said in an online chat about the checkm8.info service. “Either way I don’t support the practice and neither does the checkra1n jailbreak and checkra1n team.”
Checkm8.info only works for devices running iOS versions 12 to 14.8.1, according to checkm8.info’s website. That’s because checkm8 only works on older iPhones devices, up to the iPhone X, as it exploits an older version of the iPhone’s bootrom, the first code that an iPhone runs when it turns on. Newer iPhones have updated bootrom code that is not vulnerable to checkm8.
Activation Lock is enabled on an Apple device when the user sets up Find My, the Apple service that lets people track the location of their iPhone, Mac, or Apple Watch. After that, anyone who wants to erase or reactivate the device—something that would be vital for resellers—needs to enter the relevant Apple ID password.
A video on checkm8.info’s website shows how simple the process of using the checkm8.info tool is. A user downloads the software, installs it, opens it up, then plugs in their target device to their Mac or PC.
“Get ready for the jailbreak!” the video’s female narrator says at one point. The video then shows the checkra1n jailbreak running on a device.
Ordinarily, if a user was running the checkra1n jailbreak themselves, that would be the end of the process. But checkm8,info, in its