In a recent discovery, our research team uncovered a fake VS-code extension—truffelvscode—typosquatting the popular truffle for VS-code extension. This extension serves as a trojan horse for multi-stage malware. This blog takes a closer look at how the malicious extension operates, its obfuscation techniques, and IOCs related to this incident.
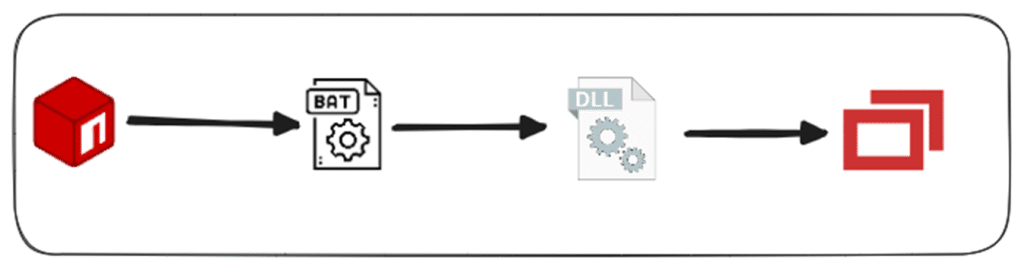
Figure 1. Attack chain
VS code extensions
VS Code extensions are add-ons that enhance Visual Studio Code by adding new features, themes, debuggers, and other integrations. This helps developers customize their workflow, improve code quality, and integrate with tools like Git, Docker, and even AI-powered coding assistants. Extensions are installed from the VS Code Marketplace.
Package analysis
The package was published 5 days ago on Feb 1, 2025. Upon examining the code, the package includes only two files, package.json, and an index.js file. The package.json file looks legitimate with no irregular installation scripts, but it has the same description as the original truffle extension: “Build, debug and deploy smart contracts on EVM-compatible blockchains.”

Figure 2. Legitimate package.json file with the original extension description
Looking at the index.js file, a heavily obfuscated code was revealed. Examining this file a little deeper, and with the help of a deobfuscator tool, we were able to reveal an ‘exec’ command at the end of the file, which connects to an external host for downloading and executing the first stage of the malware.

Figure 3. Obfuscated index.js file with the malicious exec command
The multi-stage attack chain
The attack is structured in several stages, each building on the previous one to eventually provide the attacker with remote control of the compromised system.
Stage 1: Downloading an obfuscated batch file
Upon execution, the obfuscated index.js file initiates a download of an obfuscated batch file. Notably, this batch file is itself obfuscated using the Abobus-obfuscator, a tool that significantly complicates static analysis. The obfuscation not only hides the script’s true purpose but also makes detection and reverse-engineering more difficult for automated analysis tools.

Figure 4. Obfuscated batch file
Stage 2: Executing a malicious DLL
To understand the behavior of this obfuscated batch file, we executed it in an isolated environment. Once executed, we found that the batch file was programmed to download a dynamic-link library (DLL) file using silent powershell WebRequest invocation—the second stage of the malware. After downloading, the batch file immediately executes this DLL, which serves as a critical component in the attack chain and acts as a launcher for the next phase of the infection.

Figure 5. Hidden PowerShell execution, downloading second stage DLL
Stage 3: Installing a preconfigured ScreenConnect client and gaining remote access to the compromised machine
To examine the suspicious DLL, we ran it through the any.run service, an online sandbox for automatically and dynamically dissecting malware behaviors. Looking at the exported report, we immediately saw the goal of this DLL execution: download and run the third and final stage of the malware.

Figure 6. Any.run report, revealing the third stage of the malware
This stage involves downloading and executing a ScreenConnect installer, which is typically known as a legitimate remote desktop application. In our case, after unzipping the installer, in order to get some knowledge on the files it will drop in our machine, we saw a system.config file that contained the preconfigured remote host, port, and encryption key, which will configure the ScreenConnect, to immediately create a connection between the compromised machine and the attacker machine.

Figure 7. ScreenConnect configuration file, preconfiguring the remote host and port
Fina



8 Comments
tomabai
We discover a fake vscode extension that serves a multi-stage malware on npm, Inc.
The package uses javascript obfuscation for downloading the first stage of the malware, than it uses a heavily obfuscated batch file to conntinue into the second phase.
Lastly it leverages preconfigured ScreenConnect remote desktop installer to communicate with the compromised machine.
axsharma
Interesting, blogged about this Feb 5th https://www.sonatype.com/blog/fake-vs-code-extension-on-npm-…
unsnap_biceps
I run little snitch on Mac, but I don't have similar software for windows. Is there something folks would recommend or is the windows platform hostile to those sort of tools?
0cf8612b2e1e
What’s the best way to isolate VS Code+extensions? Do I have to fully run it in a VM? Use one of those third party flatpak builds (of unknown provenance) and disable networking via flatpak mechanisms?
TZubiri
Couldn't be me.
Psa: reduce your installs of things from the internet
userbinator
NPM, why am I not surprised… and this broadly applies to the JS ecosystem.
When people delegate their brains to others, their own judgment naturally deteriorates and it makes them much easier to fool.
nailer
There's a nice new site called https://daily.dev, but they keep bugging me to install a browser extension. The idea a website needs access to somewhere I make financial transactions is horrifying.
dimal
Seems like with deno, setting granular permissions for only what’s necessary, you might be able to block an attack like this. I’m just getting started with deno, though, so I’m not sure, but it looks doable to me.